Note: The original content of this post was first published on Medium on October 26th, 2017. It was one of my most cited articles, and remains an operative view on value capture in the web3 stack at CoinFund today.
Searching for investment criteria in the functionality stack
In Fat Protocols, my fellow Brooklynite Joel Monegro insightfully draws parallels between the Internet protocols of the 1990s and the blockchain-based protocols of the 2010s. Early Internet protocols have provided massive value, he explains, but have been “thin” — meaning that monetization has historically occurred in an industrious, “fat” application layer built on the protocol. As scarce digital assets enable decentralized value and information networks, the protocols which they implement are now “fat” — monetizable at the network level using a cryptoeconomics or token — while the application layer is “thin”. Decentralized applications can still be monetized, but are much more focused on interoperability with the underlying data layer.
This view of blockchain networks is an important observation which has had profound implications for the way blockchain investments are structured*, also *discussed in CoinFund’s piece on blockchain investing. Specifically, it has taken traditional investors a market cycle with Bitcoin startups to realize that private equity of centralized companies is usually the sub-optimal method of investing in decentralized networks. But that was last summer. This summer we have cryptofunds, VC funds that can allocate capital toward token and hedge fund investments (!), SAFTs, smart contract vesting, options for cryptoassets, token-based engagement agreements, and other technology which collectively provides a set of investment tools for exposure to the growth of value networks. When investors take the time to understand and experiment with the complexity of blockchain’s new asset class, its issuance, and its lifecycle, they can make informed decisions about how to best structure investments into it.
The characterization of value networks as fat protocols has helped to underscore the need for these new investing methodologies and to outline a solution: investment for exposure to the network’s cryptoeconomics. However, the issue is that it’s easy to misconstrue the idea of fat protocols as an investment criteria. We now find investors deploying hard filters on “protocol tokens” when evaluating opportunities. I suppose we all wish that TCP/IP was “fat” and we had invested in it in 1992. In my opinion, though, this kind of investment strategy espoused by cryptoinvestors is a misapplication of Joel’s characterization of value networks.
According to some investors, there is an investment thesis based on the idea of fat protocols which goes something like this:
If you invest in an application token, then you are subject to a 95% startup failure rate (or more!) and if you invest in a protocol token you diversify across all applications built on that protocol. It’s better to diversify across protocols than across applications, because protocols are more applicable and capture the value of everything built on top of them. Base protocols will capture more value than everyone else (alas, if only TCP/IP was a fat protocol!). Therefore, invest in protocol tokens, not application tokens.
I claim that, by itself, this thesis is a highly imprecise, subjective, and therefore sub-optimal investment criteria. I also claim that much value generated within decentralized networks will never make it down into the base protocol layers. We should try to get more precise on the interaction and value flows between layers of the functionality stack of network software.
Alice doesn’t know where the protocol ends
When we talk about protocols in a blockchain investing context, we are usually not being very precise at all. A protocol is simply a collection of rules, behaviors, and formats that specify a communication standard between two or more nodes on a network. That’s extraordinarily general, and we can therefore regard a large number of decentralized applications or platforms as protocols in their own right.
Using just technical intuition, it is obvious that every layer of functionality is simultaneously a protocol for the stack above it and an application of the stack below it. TCP/IP is an application of a complicated stack of network hardware while being a protocol for data transfer between computers. HTTP is a protocol for serving structured Web data and an application of TCP/IP. Higher in the stack, dapps like Augur are applications of Ethereum’s protocol as well as data storage protocols like IPFS. Twitter is, after all, a microblogging protocol with thousands of applications built upon its API, including Twitter’s. Finally, James Childs-Maidment’s stateless smart contracts are an application of Ethereum and the protocol serving Leeroy’s centralized UX application. In short, you can draw a protocol-application boundary at any level of abstraction you like along the functionality stack.
The literal property of being a protocol is not that to which protocol fatness refers. Fat protocols refer to value and information networks — open networks that maintain compact ownership of data which they are able to monetize through cryptoeconomics. It is therefore important to understand how value flows through the layers of the functionality stack and how a given layer might capture that value.

The protocol-application boundary is an abstract separator between two sections of the functionality stack.
If “protocols” are to be the filter for better investment decisions presumably because they offer desirable characteristics such as greater diversification and bigger upside, then we should be able explain how they receive, accrue, and transfer value. Specifically, we should be able to explain why one protocol-application boundary has better characteristics for investment than another.
Good luck with TCP/IP-proximate protocol investing
Quite simply, the intuition that protocols lower in the stack tend to be more widely applicable and therefore offer more diversification is incorrect in general. In fact ‘proximity to TCP/IP’ is a questionable criteria for an investment expecting enhanced diversification. To diversify across the functionality layers above it, a protocol must first capture some market share to serve them.
The blockchain era is not like the days of TCP/IP which had only a single practical competitor and whose adoption required the coordination of governments, corporations, and standards bodies all over the world. Today’s decentralized protocol development proceeds on the backs of small, agile, open source teams who competitively produce a growing number of protocols with very general and overlapping functionality. Very clearly, widespread speculative trading of token supplies today cause disincentives for interoperability: everyone wants to build their own protocol to capture more value. Consider the number of individual decentralized protocols for the same concepts of stable currencies, asset-backed lending, exchange, and social media. If you choose the “wrong” implementing protocol, you may be investing in a siloed stack of dependencies which, just like an application, has a complex and competitive market.
Unlike networking protocols of the 1970s which were “technically so distinct that no mutual communication was allowed”, every set of decentralized protocols built on the same platform, such as Ethereum, are baseline interoperable. (For those that aren’t, there are interoperability platforms such as Cosmos or Polkadot and, naturally, those protocols live higher up the stack, not lower.) Even protocol nepotism and activist investorism — how investors are so fond of building “ecosystems” of their own interconnected portfolio companies — won’t work. In an outcome for protocol market share where many protocols win, an investor is probably better off diversifying across the protocol silos of their competitors.

In reality, protocol stacks are separated into dependency silos which compete for data, adoption, and complicated value flows.
In summary, picking the right base protocol is not much different from picking the right startup or the right application from a diversification perspective. If we posit that a few major procotols will win, then our portfolio has a similar failure rate to a portfolio of consumer-proximate applications. If, on the other hand, we suppose that protocols will coexist and interoperate, then we would have been better off investing in their interoperability which lives higher in the stack.
Oops, we left all our value in the application
In general, the ability of a base protocol to capture the value of its higher application stack is thoroughly situational and has a complicated relationship with the protocols underneath. Simple examples adequately demonstrate this.
Augur projects utilization onto Ethereum, not value.
Augur is a three-sided cryptoeconomy of market creators, market resolvers, and prediction traders. A speculative increase in the price of REP has no impact on a trader, who might never even own REP nor requires REP to trade markets. However, utilization of Augur very much drives the price of REP fundamentally, through a kind of perpetuity valuation function. Simultaneously, the utilization of Augur is reflected in Ethereum through a very different function — the transaction fees paid to the network to execute the Augur protocol. (Indeed, every transaction in the Augur application is a transaction on Ethereum.)
If we draw a boundary between Ethereum as the protocol and Augur as its application, then Ether gives exposure to the utilization of Augur but not its value. This is merely a projection of value flow from Augur onto Ethereum. If one wishes to capture the fundamental value of the Augur platform, she should probably hold REP.
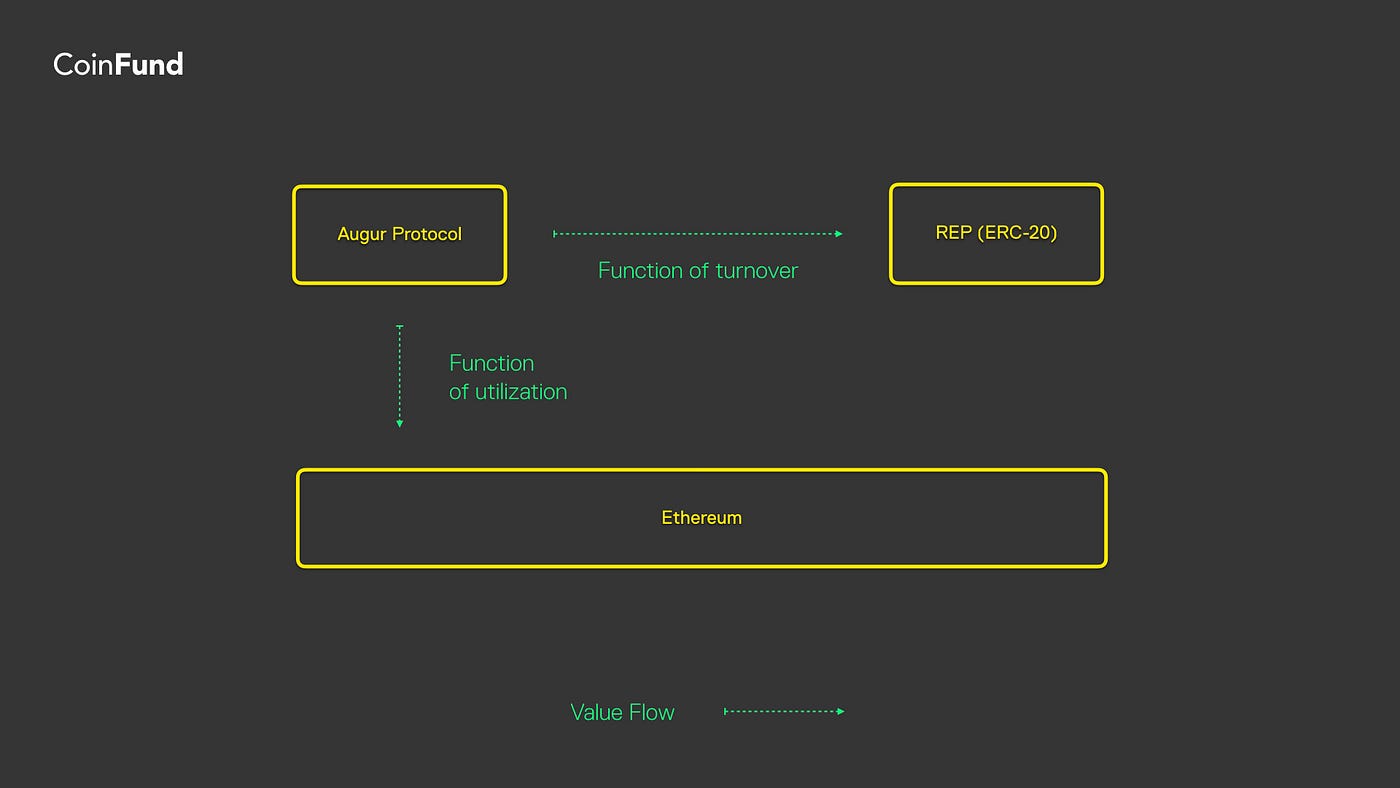
(1) Augur projects its utilization onto Ethereum through transaction volume and network fees. (2) Augur projects value onto REP as a function of the future discounted cash flows associated with the platform’s trading turnover. (3) Utilization value and turnover value are largely independent and uncorrelated.
Leeroy monetizes through direct use.
Similarly, holding Ether will give you exposure only to the utilization of Leeroy, but not its value. Leeroy itself doesn’t have a token and is therefore not a fat protocol. But that’s exactly the point: to invest in the operational throughput of Leeroy by proxy of a base protocol requires that one, literally, must become an Ethereum miner. On the other hand, Leeroy’s stateless smart contract architecture creates a much more compelling monetization alternative in its centralized application layer (Leeroy’s so-called “filter”). If you’re actually earning money as an influencer on Leeroy, that might be the most efficient way of capturing non-operational turnover of this platform.
Consumer-proximate tokens win the short term.
Finally, taking a step back, 2017 has marked the spillover of blockchain technologies into the greater tech markets. CoinFund has been lucky to work with the first major technology companies to pioneer cryptoeconomics-based business models, Kik Interactive and YouNow. Furthermore, this trend continues as seasoned entrepreneurs have grasped the prospective value of ad-free business models based on cryptoassets and micropayments. As more and more mainstream user bases are introduced to cryptoeconomics, the short to medium term growth lies in successful consumer-proximate applications. In fact, any on-chain protocol built on a blockchain today is likely to be left behind in this growth opportunity due to its scalability bottleneck. Consumer-facing applications built by experienced companies with resources and in-house tech teams will need to shore up mainstream-friendly experiences. This means value will be flowing into semi-centralized niches of the functionality stack, into off-chain solutions, and into managed experiences.
These views seem to suggest that diversification needs to happen vertically in the protocol stack, not horizontally in its base layers for most investors. And if your investors are playing the base protocol game, it might be time to get more precise about value flow theses.
Conclusion
Investors who draw unqualified boundaries between “application tokens” and “protocol tokens” are silly. There, I said it. Yes, value generally flows down the functionality stack, but it does not necessarily pool in base protocols — it gets siloed, redirected, stuck, diluted, and denatured along the way. Every transfer of value between layers requires an analysis of that transfer, and not every transfer of value works the same way. Holding Ether may expose investors to the utilization of the stack above more than it exposes them to its excess value. Holding tokens for applications which bring millions of users to cryptoeconomic systems may be a far superior medium term strategy for capturing blockchain’s growth curves. Every protocol-application boundary requires its own analysis. We have a lot of work to do to get more precise about protocols and understand the relationships between layers in the functionality stack.
Disclaimer: Neither the author of this article, nor CoinFund, provide investment, financial, or legal advice. This site cannot substitute for professional advice and independent factual verification. The content provided on this site is for informational purposes only and should not be construed as any kind of solicitation for investment in any investment opportunity.